Advertisements
Traditional symmetric key ciphers
General idea of symmetric-key cipher
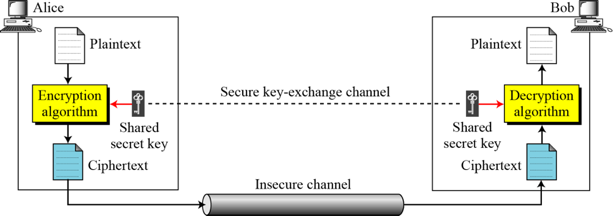
- The original message from Alice to Bob is called plaintext;
- the message that is sent through the channel is called the ciphertext.
- To create ciphertext from plaintext, Alice uses encryption algorithm & shared secret key.
- To create plaintext from ciphertext, Bob uses a decryption algorithm & same secret key.
Kerckhoff’s principle: one should always assume that the adversary(Eve) knows the encryption/decryption algorithm. The resistance of the cipher to attack must be based only on the secrecy of the key.
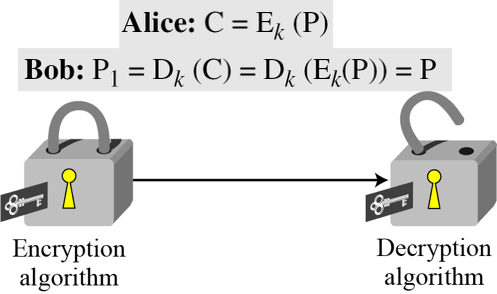
If P is the plaintext, C is the ciphertext, and K is the key,
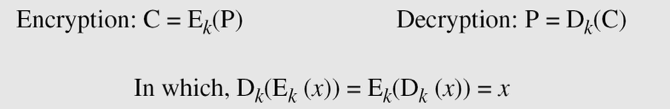
We assume that Bob creates P1; we prove that P1 = P: